How To Write Security Incident Report (Template Inside)
Discover how to write effective security incident reports with our guide. Learn about best practices, and key components, and get a free template to edit freely.

Whether it's a case of theft, vandalism, a cyberattack, or a workplace injury, having a detailed account of what happened can help you identify vulnerabilities and improve safety protocols.
In this article, we'll explore the best practices for writing a complete security incident report and provide you with a handy template to get started.
Read on to learn:
- Key components of a security incident report
- Tips for writing clear and concise reports
- How to use our security incident report template
- Examples of different types of incident reports
- How Belfry helps with reporting and managing security operations at scale
Before we start sharing tips and examples, let’s refresh you on what a security incident report actually is.
What is a security incident report?
A security incident report is a record of any event that risks the safety of an organization. It’s a detailed account of what happened, when and where it occurred, and who was involved.
They play a vital role in understanding the nature of security breaches, identifying vulnerabilities, and preventing future incidents.
Whether it's a case of theft, vandalism, a cyberattack, or even something like a workplace injury, a well-written security incident report provides valuable insights that can be used to improve safety protocols and protect assets.
These reports are also vital for maintaining accountability and providing accurate record-keeping. They can be used for investigations, insurance claims, legal proceedings, and even to demonstrate compliance with industry regulations.
In essence, a security incident report acts as a formal, reliable record of events, painting a clear picture of what transpired and how it was handled.
Key components of a security incident report
Now, let's break down the essential parts of a solid security incident report:
Basic incident details
First things first, we need to establish the when and where. This section should include:
- Date and time of the incident: Be precise. Record the exact date and time the incident occurred. This helps establish a clear timeline of events.
- Location of the incident: Specify the precise location where the incident took place. Include details like building name, room number, or even specific landmarks if it happened outdoors.
Description of the incident itself
Now, let's get into the nitty-gritty of what happened. This section calls for a detailed narrative of the incident, including:
- A chronological account of events: Describe the incident as it unfolded, step-by-step. Start with what led up to the incident, then describe the incident itself, and finally, what happened immediately after.
- Actions taken during the incident: Outline the immediate steps taken by security personnel or others involved. This might include things like intervention, evacuation, or first aid.
- Outcomes of the incident: Describe the immediate results of the incident. Was anyone injured? Was there any property damage? Were any suspects apprehended?
Involved parties and witnesses
It's important to identify everyone involved. This section should list:
- Names and roles of all parties involved: This includes victims, suspects, security personnel, and anyone else who played a role in the incident.
- Witness statements: Gather statements from any witnesses who observed the incident. These accounts can provide valuable perspectives and corroborating evidence.
Evidence and documentation
This section focuses on gathering and documenting any evidence related to the incident:
- Types of evidence: This might include photos, video footage, security logs, physical evidence, or any other relevant materials.
- Importance of thorough documentation: It’s vital to document all evidence accurately and transparently. This ensures its integrity and admissibility if needed for investigations or legal proceedings.
Actions taken
Finally, let's talk about what happened after the incident:
- Response steps: Detail the immediate actions taken to address the incident, such as medical assistance, law enforcement notification, or internal reporting procedures.
- Mitigation measures: Outline any steps taken to prevent a similar incident from happening again. This might include things like increased security patrols, improved lighting, or staff training.
- Follow-up actions: Describe any ongoing or planned activities related to the incident, such as investigations, disciplinary actions, or insurance claims.
By including these key components in your security incident report, you'll create a complete and informative document that can be used to understand, address, and prevent future incidents.
Best practices for writing a detailed security incident report
Now that we know what goes into a security incident report, let's dive into some best practices for writing one that is truly effective. Follow these tips:
Keep it simple by using clear and concise language
Avoid using jargon, technical terms, or overly complex language. Remember, your report may be read by people who don't have a technical background.
Use plain language and get to the point. This will help you make sure that your report is easy for everyone to read and understand.
Include only the facts
A security incident report should be an objective account of what happened. Stick to the facts and avoid including personal opinions, assumptions, or speculation.
Focus on providing factual descriptions of the incident, the people involved, and the actions taken. Going with this approach will help you maintain the integrity and credibility of your report.
Follow a structured format
Consistency is key when it comes to writing effective security incident reports. Using a security incident report template can be very helpful.
Using a template helps in making sure that you include all the vital information and that your reports follow a consistent format. A structured approach makes it easier to read, understand, and compare reports over time. Plus, it helps confirm that you don't miss any key details.
Always review and proofread
Before submitting your report, take the time to carefully review and proofread it. Check for any errors in grammar, spelling, punctuation, and factual accuracy.
A well-written and error-free report looks professional while ensuring that the information is clear and easily understood.
Create templates and store incident reports digitally
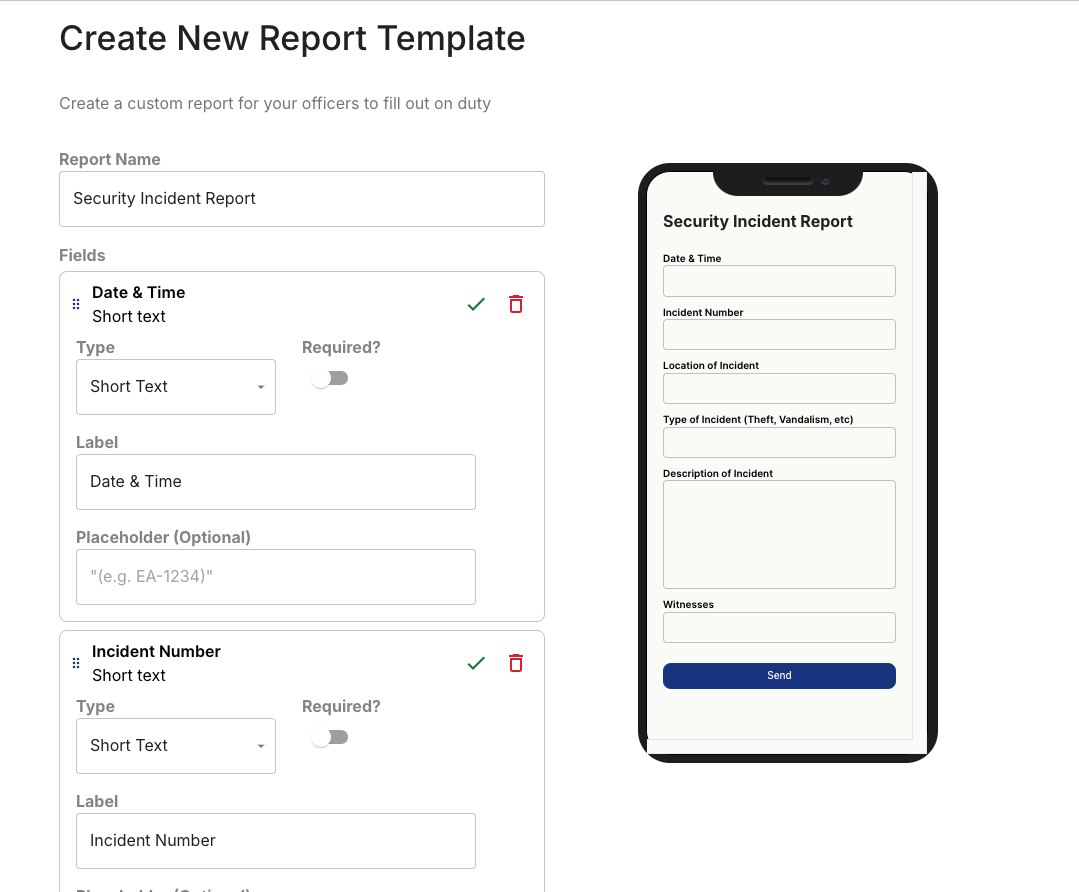
If you don’t want to mess with a bunch of documents and spend time organizing them, you can use a security management platform like Belfry.
You can create a template, and then guards can fill it out on their phones while they work or whenever they have a minute.
For more details, check out more about Belfry below, as this is only one feature. You can also store images from incidents, track security guard licensing, and much more.
Security incident report template
To make things even easier for you, we've created a handy security incident report template that you can use right away. You can access the template directly here.
Three security incident report examples
Let's take a look at three security incident report examples featuring common incidents you might encounter. These examples will give you a better idea of how to structure your reports:
Example 1: Theft incident report
Imagine a retail store where a shoplifter attempts to steal merchandise. A security guard observes the suspect concealing items and attempts to apprehend them. This is what a report of that incident would look like:
- Incident number: 2024-11-20-001
- Date and time of incident: November 20, 2024, 3:15 PM
- Location: Main sales floor, "XYZ Retail Store," 123 Main Street
- Description: Security guard observed a suspect (Description: male, approximately 6 feet tall, wearing a blue jacket and jeans) concealing merchandise (Items: 2 pairs of designer sunglasses) in a backpack.
The guard approached the suspect and identified themselves. The suspect attempted to flee but was apprehended by the guard. Police were called, and the suspect was arrested.
- Involved parties:
- Suspect: John Smith (apprehended)
- Security guard: Jane Doe
- Witness: Store manager, Peter Jones
- Evidence: Security camera footage, witness statements, recovered stolen merchandise.
- Actions taken: Police were notified and responded to the scene. The suspect was arrested and charged with theft. Stolen merchandise was recovered.
Example 2: Vandalism incident report
Let's say someone vandalizes a public park by spray-painting graffiti on a monument. A witness reports the incident to park security. The incident report of this act of vandalism would look like this:
- Incident number: 2024-11-20-002
- Date and time of incident: November 19, 2024, 10:00 PM (approximate)
- Location: Central Park, near the main fountain
- Description: Graffiti was discovered on the historical monument in Central Park. A witness reported seeing a group of individuals (description: 3 teenagers wearing dark hoodies) in the area around the time of the incident.
- Involved parties:
- Witness: Name withheld (contact information recorded)
- Evidence: Photos of the graffiti, witness statement.
- Actions taken: Police were notified. Park maintenance was contacted to remove the graffiti. Increased security patrols were implemented in the area.
Example 3: Workplace injury report
An employee in a warehouse trips and falls, injuring their ankle. This incident report could look like this:
- Incident number: 2024-11-20-003
- Date and time of incident: November 20, 2024, 9:45 AM
- Location: Warehouse receiving area, "ABC Logistics," 456 Oak Avenue
- Description: Employee (Name: Maria Garcia) tripped over a pallet jack while unloading a delivery truck. Ms. Garcia sustained an injury to her right ankle.
- Involved parties:
- Injured employee: Maria Garcia
- Witness: Warehouse Supervisor, David Lee
- Evidence: Witness statement, photos of the incident location.
- Actions taken: First aid was administered to Ms. Garcia. An ambulance was called, and Ms. Garcia was transported to the hospital. The incident location was inspected for safety hazards.
These security incident report examples illustrate how a consistent format and clear language can be used to document a variety of incidents. Remember to tailor the report to the specific circumstances of each event, making sure all relevant details are captured accurately.
How Belfry can support security incident reporting
We've explained the essentials of writing a detailed security incident report and even provided a template. But did you know that an end-to-end security management platform like Belfry can simplify the process and improve the quality and impact of your incident reporting?
Here's how Belfry can take your security incident reporting to the next level:
- Real-time incident capture: Belfry equips your security personnel with a modern, user-friendly app that allows for instant reporting of incidents right from their smartphones.
Belfry helps you confirm that crucial details are captured accurately and promptly, eliminating delays and potential inaccuracies of traditional reporting methods.
- Multimedia evidence integration: With Belfry, your team can easily attach photos and videos directly to incident reports. This feature helps provide valuable visual documentation, creating a more exhaustive and impactful record of events.
- Automated report distribution: Belfry simplifies the flow of information by automatically routing incident reports to designated recipients. Belfry ensures that relevant stakeholders are immediately notified and can take appropriate action without delay.
- Centralized incident log: All incident reports are securely stored and organized within Belfry's platform, creating a centralized repository for easy access and analysis. We facilitate trend tracking and informed decision-making regarding security protocols.
- Out-of-the-box analytics: Belfry’s analytics dashboards give you and your clients insights (e.g., most common incident types, most frequent days / times of incidents) to better plan security personnel placements.
- Improved accuracy and accountability: By simplifying and standardizing the reporting process, Belfry promotes greater accuracy and consistency in incident documentation. This supports accountability and provides reliable records for possible legal proceedings.